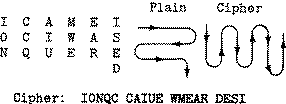Introduction
Legal and Ethical
Categories of law
Differences between legal and Ethic
Ethics concept in Information Security
Protecting programs and Data
Information and Law
Objectives of Understanding Legal Section
Therefore, there are three motivations for studying the legal section
to know what protection the law provides for computers and data;
to appreciate laws that protect the rights of others with respect to computers, programs, and data; and
to understand existing laws as a basis for recommending new laws to protect computers, data, and people.
::->There are three common used ways to provide protections by laws:
@Copyright
Copyright gives the author/programmer exclusive right to make copies of the expression and sell them to the public. That is, only the author can sell copies of the author’s book (except, of course, for booksellers or others working as the agents of the author).
Copyrights for Computer Works
The algorithm is the idea, and the statements of the programming language are the expression of the idea.
Therefore, protection is allowed for the program statements themselves, but not for the design: copying the code intact is prohibited, but reimplementing the algorithm is permitted.
Examples of Copyrights
A second problem with the copyright protection for computer works is the requirement that the work be published.
A program may be published by distributing copies of its object code, for example on a disk. However, if the source code is not distributed, it has not been published.
An alleged infringer cannot have violated a copyright on source code if the source code was never published.
A copyright controls the right to copy and distribute; it is not clear that allowing distributed access is a form of distribution in distributed system.
@Patent
Patents are unlike copyrights in that they protect inventions, not works of the mind.
The distinction between patents and copyrights is that patents were intended to apply to the results of science, technology, and engineering, whereas copyrights were meant to cover works in the arts, literature, and written scholarship.
The patents law excludes newly discovered laws of nature … [and] mental processes.
Computer Objects
The patent has not encouraged patents of computer software.
For a long time, computer programs were seen as the representation of an algorithm was a fact of nature, which is not subject to patent.
There was a case on a request to patent a process for converting decimal numbers into binary. The Supreme Court rejected the claim, saying it seemed to attempt to patent an abstract idea, in short, an algorithm. But the underlying algorithm is precisely what most software developers would like to protect.
@Trade Secret
A trade secret is information that gives one company a competitive edge over others. For example, the formula for a soft drink is a trade secret, as is a mailing list of customers, or information about a product due to be announced in a few months.
The distinguishing characteristic of a trade secret is that it must always be kept secret. The owner must take precautions to protect the secret, such as storing it in a safe, encrypting it in a computer file, or making employees sign a statement that they will not disclose the secret.
Trade secret protection applies very well to computer software.
The underlying algorithm of a computer program is novel, but its novelty depends on nobody else’s knowing it.
Trade secret protection allows distribution of the result of a secret (the executable program) while still keeping the program design hidden.
Trade secret protection does not cover copying a product (specifically a computer program), so that it cannot protect against a pirate who sells copies of someone else’s program without permission.
However, trade secret protection makes it illegal to steal a secret algorithm and use it in another product.
Why Computer Crime is Hard to Define?
Understanding
*Neither courts, lawyers, police agents, nor jurors necessarily understand computers.
Fingerprints
*Polices and courts for years depended on tangible evidence, such as fingerprints. But with many computer crimes there simply are no fingerprints, no physical clues.
Form of Assets
*We know what cash is, or diamonds, or even negotiable securities. But are 20 invisible magnetic spots really equivalent to a million dollars?
Juveniles
*Many computer crimes involve juveniles. Society understands immaturity and can treat even very serious crimes by juveniles as being done with less understanding than when the same crime is committed by an adult.
Type of Crimes Committed
Telecommunications Fraud
*It is defined as avoiding paying telephone charges by misrepresentation as a legitimate user.
Embezzlement
*It involves using the computer to steal or divert funds illegally.
Hacking
*It denotes a compulsive programmer or user who explores, tests, and pushes computers and communications system to their limits - often illegal activities.
Automatic Teller Machine Fraud
*It involves using an ATM machine for a fraudulent activity - faking deposits, erasing withdrawals, diverting funds from another person’s account through stolen PIN numbers.
Records Tampering
*It involves the alteration, loss, or destruction of computerised records.
Acts of Disgruntled Employees
*They often use a computer for revenge against their employer.
Child Pornography and Abuse
*They are illegal or inappropriate arts of a sexual nature committed with a minor or child, such as photographing or videotaping.
Drug Crimes
*Drug dealers use computers to communicate anonymously with each other and to keep records of drug deals.
Organised Crime
*For all kinds of crime, the computer system may be used as their tools.
Summary
Firstly, the legal mechanisms of copyright, patent, and trade secret were presented as means to protect the secrecy of computer hardware, software and data.
However, these mechanisms were designed before the invention of computer, so their applicability to computing needs is somewhat limited.
Meanwhile, program protection is especially desired, and software companies are pressing the courts to extend the interpretation of these means of protection to include computers.
Secondly, relationship between employers and employees, in the context of writers of software. Well-established laws and precedents control the acceptable access an employee has to software written for a company
Thirdly, some difficulties of in prosecuting computer crime. In general, the courts have not yet granted computers, software, and data appropriate status considering value of assets and seriousness of crime. The legal system is moving cautiously in its acceptance of computers.
What are Ethics?
Society relies on ethics or morals to prescribe generally accepted standards of proper behaviour.
An ethic is an objectively defined standard of right and wrong within a group of individuals.
These ethics may influence by religious believe. Therefore, through choices, each person defines a personal set of ethical practices.
A set of ethical principles is called and ethical system.
Differences of The Law and Ethics
Firstly, laws apply to every one, even you do not agree with the laws. However, you are forced to respect and obey the laws.
Secondly, there is a regular process through the courts for determining which law supersedes which if two laws conflict.
Thirdly, the laws and the courts identify certain actions as right and others as wrong. From a legal standpoint, anything that is not illegal is right.
Finally, laws can be enforced, and there are ways to rectify wrongs done by unlawful behaviour.
Contrast of Law Versus Ethics
Thursday, October 22, 2009
LEC 10:: Legal and Ethical Issues in Computer Security
Posted by SeCuRiTy LiFe.. at 6:23 PM 0 comments
LEC 9:: Intrusion Detection System
Intruders
Security Intrusion & Detection
Types of IDS
*HIDS
*NIDS
*DIDS
IDS Techniques
SNORT
Honeypots
An Intrusion detection system (IDS) is software and/or hardware designed to detect unwanted attempts at accessing, manipulating, and/or disabling computer systems, mainly through a network, such as the Internet. These attempts may take the form of attacks, as examples, by crackers, malware and/or disgruntled employees. An IDS cannot directly detect attacks within properly encrypted traffic.
An intrusion detection system is used to detect several types of malicious behaviors that can compromise the security and trust of a computer system. This includes network attacks against vulnerable services, data driven attacks on applications, host based attacks such as privilege escalation, unauthorized logins and access to sensitive files, and malware (viruses, trojan horses, and worms).
An IDS can be composed of several components: Sensors which generate security events, a Console to monitor events and alerts and control the sensors, and a central Engine that records events logged by the sensors in a database and uses a system of rules to generate alerts from security events received. There are several ways to categorize an IDS depending on the type and location of the sensors and the methodology used by the engine to generate alerts. In many simple IDS implementations all three components are combined in a single device or appliance.
IDS Terminology
Alert/Alarm- A signal suggesting a system has been or is being attacked [1].
True attack stimulus- An event that triggers an IDS to produce an alarm and react as though a real attack were in progress [1].
False attack stimulus- The event signaling an IDS to produce an alarm when no attack has taken place [1].
False (False Positive)- An alert or alarm that is triggered when no actual attack has taken place [1].
*False negative- A failure of an IDS to detect an actual attack.
*Noise- Data or interference that can trigger a false positive .
*Site policy- Guidelines within an organization that control the rules and configurations of an IDS .
*Site policy awareness- The ability an IDS has to dynamically change its rules and configurations in response to changing environmental activity .
*Confidence value- A value an organization places on an IDS based on past performance and analysis to help determine its ability to effectively identify an attack .
*Alarm filtering- The process of categorizing attack alerts produced from an IDS in
order to distinguish false positives from actual attacks.
Types of Intrusion-Detection systems
There are three main types of systems in which IDS can be used : network, applications and hosts.
In a network-based intrusion-detection system (NIDS), the sensors are located at choke points in network to be monitored, often in the demilitarized zone (DMZ) or at network borders. The sensor captures all network traffic and analyzes the content of individual packets for malicious traffic.
In systems, PIDS and APIDS are used to monitor the transport and protocols for illegal or inappropriate traffic or constructs of a language. For example forged SQL queries attempting to delete database records, virus in emails.
In a host-based system, the sensor usually consists of a software agent, which monitors all activity of the host on which it is installed. For example attempt to modify the master boot record, keylogger, file access.
Hybrids for the two later systems also exist.
Network intrusion detection system (NIDS)
It is an independent platform which identifies intrusions by examining network traffic and monitors multiple hosts. Network Intrusion Detection Systems gain access to network traffic by connecting to a hub, network switch configured for port mirroring, or network tap. An example of a NIDS is Snort.
Protocol-based intrusion detection system (PIDS)
It consists of a system or agent that would typically sit at the front end of a server, monitoring and analyzing the communication protocol between a connected device (a user/PC or system) and the server. For a web server this would typically monitor the HTTPS protocol stream and understand the HTTP protocol relative to the web server/system it is trying to protect. Where HTTPS is in use then this system would need to reside in the "shim", or interface, between where HTTPS is un-encrypted and immediately prior to its entering the Web presentation layer.
Application protocol-based intrusion detection system (APIDS)
It consists of a system or agent that would typically sit within a group of servers, monitoring and analyzing the communication on application specific protocols. For example, in a web server with a database this would monitor the SQL protocol specific to the middleware/business logic as it transacts with the database.
Host-based intrusion detection system (HIDS)
It consists of an agent on a host which identifies intrusions by analyzing system calls, application logs, file-system modifications (binaries, password files, capability/acl databases) and other host activities and state. An example of a HIDS is OSSEC.
Hybrid intrusion detection system
It combines two or more approaches. Host agent data is combined with network information to form a comprehensive view of the network. An example of a Hybrid IDS is Prelude.
Intrusion detection systems can also be system-specific using custom tools and honeypots.
Posted by SeCuRiTy LiFe.. at 6:21 PM 0 comments
LEC 8:: FIREWALL

A firewall is a part of a computer system or network that is designed to block unauthorized access while permitting authorized communications. It is a device or set of devices configured to permit, deny, encrypt, decrypt, or proxy all (in and out) computer traffic between different security domains based upon a set of rules and other criteria.
Firewalls can be implemented in either hardware or software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria.
There are several types of firewall techniques:
1. Packet filter: Packet filtering inspects each packet passing through the network and accepts or rejects it based on user-defined rules. Although difficult to configure, it is fairly effective and mostly transparent to its users. In addition, it is susceptible to IP spoofing.
2. Application gateway: Applies security mechanisms to specific applications, such as FTP and Telnet servers. This is very effective, but can impose a performance degradation.
3. Circuit-level gateway: Applies security mechanisms when a TCP or UDP connection is established. Once the connection has been made, packets can flow between the hosts without further checking.
4. Proxy server: Intercepts all messages entering and leaving the network. The proxy server effectively hides the true network addresses.
Function
A firewall is a dedicated appliance, or software running on a computer, which inspects network traffic passing through it, and denies or permits passage based on a set of rules.
It is a software or hardware that is normally placed between a protected network and an unprotected network and acts like a gate to protect assets to ensure that nothing private goes out and nothing malicious comes in.
A firewall's basic task is to regulate some of the flow of traffic between computer networks of different trust levels. Typical examples are the Internet which is a zone with no trust and an internal network which is a zone of higher trust. A zone with an intermediate trust level, situated between the Internet and a trusted internal network, is often referred to as a "perimeter network" or Demilitarized zone (DMZ).
A firewall's function within a network is similar to physical firewalls with fire doors in building construction. In the former case, it is used to prevent network intrusion to the private network. In the latter case, it is intended to contain and delay structural fire from spreading to adjacent structures.
Without proper configuration, a firewall can often become worthless. Standard security practices dictate a "default-deny" firewall ruleset, in which the only network connections which are allowed are the ones that have been explicitly allowed. Unfortunately, such a configuration requires detailed understanding of the network applications and endpoints required for the organization's day-to-day operation. Many businesses lack such understanding, and therefore implement a "default-allow" ruleset, in which all traffic is allowed unless it has been specifically blocked. This configuration makes inadvertent network connections and system compromise much more likely.
First generation - packet filters
The first paper published on firewall technology was in 1988, when engineers from Digital Equipment Corporation (DEC) developed filter systems known as packet filter firewalls. This fairly basic system was the first generation of what would become a highly evolved and technical internet security feature. At AT&T Bell Labs, Bill Cheswick and Steve Bellovin were continuing their research in packet filtering and developed a working model for their own company based upon their original first generation architecture.
Packet filters act by inspecting the "packets" which represent the basic unit of data transfer between computers on the Internet. If a packet matches the packet filter's set of rules, the packet filter will drop (silently discard) the packet, or reject it (discard it, and send "error responses" to the source).
This type of packet filtering pays no attention to whether a packet is part of an existing stream of traffic (it stores no information on connection "state"). Instead, it filters each packet based only on information contained in the packet itself (most commonly using a combination of the packet's source and destination address, its protocol, and, for TCP and UDP traffic, the port number).
TCP and UDP protocols comprise most communication over the Internet, and because TCP and UDP traffic by convention uses well known ports for particular types of traffic, a "stateless" packet filter can distinguish between, and thus control, those types of traffic (such as web browsing, remote printing, email transmission, file transfer), unless the machines on each side of the packet filter are both using the same non-standard ports.
Second generation - Application layer
The key benefit of application layer filtering is that it can "understand" certain applications and protocols (such as File Transfer Protocol, DNS, or web browsing), and it can detect whether an unwanted protocol is being sneaked through on a non-standard port or whether a protocol is being abused in any harmful way.
Third generation - "stateful" filters
From 1989-1990 three colleagues from AT&T Bell Laboratories, Dave Presetto, Janardan Sharma, and Kshitij Nigam developed the third generation of firewalls, calling them circuit level firewalls.
Third generation firewalls in addition regard placement of each individual packet within the packet series. This technology is generally referred to as a stateful packet inspection as it maintains records of all connections passing through the firewall and is able to determine whether a packet is either the start of a new connection, a part of an existing connection, or is an invalid packet. Though there is still a set of static rules in such a firewall, the state of a connection can in itself be one of the criteria which trigger specific rules.
This type of firewall can help prevent attacks which exploit existing connections, or certain Denial-of-service attacks.
::TYPES::
There are several classifications of firewalls depending on where the communication is taking place, where the communication is intercepted and the state that is being traced.
Network layer and packet filters
Network layer firewalls, also called packet filters, operate at a relatively low level of the TCP/IP protocol stack, not allowing packets to pass through the firewall unless they match the established rule set. The firewall administrator may define the rules; or default rules may apply. The term "packet filter" originated in the context of BSD operating systems.
Network layer firewalls generally fall into two sub-categories, stateful and stateless. Stateful firewalls maintain context about active sessions, and use that "state information" to speed packet processing. Any existing network connection can be described by several properties, including source and destination IP address, UDP or TCP ports, and the current stage of the connection's lifetime (including session initiation, handshaking, data transfer, or completion connection). If a packet does not match an existing connection, it will be evaluated according to the ruleset for new connections. If a packet matches an existing connection based on comparison with the firewall's state table, it will be allowed to pass without further processing.
Stateless firewalls require less memory, and can be faster for simple filters that require less time to filter than to look up a session. They may also be necessary for filtering stateless network protocols that have no concept of a session. However, they cannot make more complex decisions based on what stage communications between hosts have reached.
Modern firewalls can filter traffic based on many packet attributes like source IP address, source port, destination IP address or port, destination service like WWW or FTP. They can filter based on protocols, TTL values, netblock of originator, of the source, and many other attributes.
Commonly used packet filters on various versions of Unix are ipf (various), ipfw (FreeBSD/Mac OS X), pf (OpenBSD, and all other BSDs), iptables/ipchains (Linux).
Application-layer
Application-layer firewalls work on the application level of the TCP/IP stack (i.e., all browser traffic, or all telnet or ftp traffic), and may intercept all packets traveling to or from an application. They block other packets (usually dropping them without acknowledgment to the sender). In principle, application firewalls can prevent all unwanted outside traffic from reaching protected machines.
On inspecting all packets for improper content, firewalls can restrict or prevent outright the spread of networked computer worms and trojans. The additional inspection criteria can add extra latency to the forwarding of packets to their destination.
Proxies
A proxy device (running either on dedicated hardware or as software on a general-purpose machine) may act as a firewall by responding to input packets (connection requests, for example) in the manner of an application, whilst blocking other packets.
Proxies make tampering with an internal system from the external network more difficult and misuse of one internal system would not necessarily cause a security breach exploitable from outside the firewall (as long as the application proxy remains intact and properly configured). Conversely, intruders may hijack a publicly-reachable system and use it as a proxy for their own purposes; the proxy then masquerades as that system to other internal machines. While use of internal address spaces enhances security, crackers may still employ methods such as IP spoofing to attempt to pass packets to a target network.
Network address translation
Firewalls often have network address translation (NAT) functionality, and the hosts protected behind a firewall commonly have addresses in the "private address range", as defined in RFC 1918. Firewalls often have such functionality to hide the true address of protected hosts. Originally, the NAT function was developed to address the limited number of IPv4 routable addresses that could be used or assigned to companies or individuals as well as reduce both the amount and therefore cost of obtaining enough public addresses for every computer in an organization. Hiding the addresses of protected devices has become an increasingly important defense against network reconnaissance.
Posted by SeCuRiTy LiFe.. at 6:19 PM 0 comments
LEC 7:: WIRELESS SECURITY

Wireless LANs
IEEE ratified 802.11 in 1997.
-Also known as Wi-Fi.
Wireless LAN at 1 Mbps & 2 Mbps.
WECA (Wireless Ethernet Compatibility Alliance) promoted Interoperability.
-Now Wi-Fi Alliance
802.11 focuses on Layer 1 & Layer 2 of OSI model.
-Physical layer
-Data link layer
A wireless local area network (WLAN) links two or more devices using some wireless distribution method (typically spread-spectrum or OFDM radio), and usually providing a connection through an access point to the wider internet. This gives users the mobility to move around within a local coverage area and still be connected to the network.
Wireless LANs have become popular in the home due to ease of installation, and the increasing popularity of laptop computers. Public businesses such as coffee shops and malls have begun to offer wireless access to their customers; sometimes for free.
Types of wireless lan
::Peer to peet::
An ad-hoc network is a network where stations communicate only peer to peer (P2P). There is no base and no one gives permission to talk. This is accomplished using the Independent Basic Service Set (IBSS).
A peer-to-peer (P2P) network allows wireless devices to directly communicate with each other. Wireless devices within range of each other can discover and communicate directly without involving central access points. This method is typically used by two computers so that they can connect to each other to form a network.
If a signal strength meter is used in this situation, it may not read the strength accurately and can be misleading, because it registers the strength of the strongest signal, which may be the closest computer.
IEEE 802.11 define the physical layer (PHY) and MAC (Media Access Control) layers based on CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance). The 802.11 specification includes provisions designed to minimize collisions, because two mobile units may both be in range of a common access point, but out of range of each other.
The 802.11 has two basic modes of operation: Ad hoc mode enables peer-to-peer transmission between mobile units. Infrastructure mode in which mobile units communicate through an access point that serves as a bridge to a wired network infrastructure is the more common wireless LAN application the one being covered. Since wireless communication uses a more open medium for communication in comparison to wired LANs, the 802.11 designers also included shared-key encryption mechanisms: Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA, WPA2), to secure wireless computer networks.
::Bridge::
A bridge can be used to connect networks, typically of different types. A wireless Ethernet bridge allows the connection of devices on a wired Ethernet network to a wireless network. The bridge acts as the connection point to the Wireless LAN.
::Wireless distribution system::
A Wireless Distribution System is a system that enables the wireless interconnection of access points in an IEEE 802.11 network. It allows a wireless network to be expanded using multiple access points without the need for a wired backbone to link them, as is traditionally required. The notable advantage of WDS over other solutions is that it preserves the MAC addresses of client packets across links between access points.
An access point can be either a main, relay or remote base station. A main base station is typically connected to the wired Ethernet. A relay base station relays data between remote base stations, wireless clients or other relay stations to either a main or another relay base station. A remote base station accepts connections from wireless clients and passes them to relay or main stations. Connections between "clients" are made using MAC addresses rather than by specifying IP assignments.
All base stations in a Wireless Distribution System must be configured to use the same radio channel, and share WEP keys or WPA keys if they are used. They can be configured to different service set identifiers. WDS also requires that every base station be configured to forward to others in the system.
WDS may also be referred to as repeater mode because it appears to bridge and accept wireless clients at the same time (unlike traditional bridging). It should be noted, however, that throughput in this method is halved for all clients connected wirelessly.
When it is difficult to connect all of the access points in a network by wires, it is also possible to put up access points as repeaters.
WPA and WEP
WPA and WEP are technologies that "encrypt" the traffic on your network. That is, they scramble it so that an attacker can't make any sense of it. To unscramble it at the other end, all systems using it must know a "key" or password.
Note that WPA is now in a second generation, referred to as WPA2. Unless otherwise specified, this document uses "WPA" to refer to both.
WPA and WEP provide both access control and privacy. Privacy comes from the encryption. Access control comes from the fact that someone must know the password to use your network.
For this reason, for small networks, using WPA is enough to meet the requirements of the Wireless policy. However you will still want to make sure that any services that use a password or other private information use SSL or some other type of end to end encryption.
WEP is significantly less secure than WPA, but can be used until your equipment can be upgraded to support WPA. While WEP is widely regarded as insecure, it is still a lot better than nothing.
WPA has two modes, personal and enterprise. For small installations you'll want to use personal mode. It just requires a password. Enterprise mode is for larger installations, that have a Radius server that will support WPA.
The primary problem with WPA in personal mode is that it has a single password, which you must tell to all users. That becomes impractical for larger installations.
WPA in enterprise mode requires each user to login with their own username and password. That simplifies management in large installations, because you don't have to distribute a common password to all your users. However it is a bit more complex to implement:
* Each user's system must have special software to let the user login to the network. This software is referred to as an "802.1x supplicant".
* The access point must support WPA enterprise mode. The access point is configured to talk to a RADIUS server, which is a central server that actually checks the password.
* You must have a RADIUS server that supports WPA enterprise mode. While the RADIUS server may have its own list of usernames and passwords, it would be more common for it to talk to an LDAP or Active Directory server, so that users login to the network with the same password that they use for other services.
For this reason, most large implementations at Rutgers do not use enterprise mode. Instead they use separate gateway boxes for access control, and depend upon end to end encryption for privacy. One can argue that this is not as secure as WPA enterprise mode, but it avoids the support implications of requiring users to login to the network with an 802.1x supplicant.
Choosing a good password
It is critical to use a good password. There are attacks against WPA that will break your security if your password uses words or any other well-known sequences. WPA allows passwords as long as 63 characters. We strongly recommend using a long random password, or at the very least a long phrase (at least 20 characters, but preferably longer). The phrase should not be taken from any web site or published work. Most software saves the password, so you only need to type it once on each system.
Even better than a long phrase is a truly random password. For example, consider using http://rulink.rutgers.edu/random.php3. This generates a random 32-character hex string. You can combine two of them (and leave off one character) to get a 63-character password.
Posted by SeCuRiTy LiFe.. at 6:13 PM 0 comments
LEC 6:: SECURITY APPLICATION


Security in Email
#SMIME
S/MIME (Secure / Multipurpose Internet Mail Extensions) is a standard for public key encryption and signing of e-mail encapsulated in MIME.
S/MIME is on an IETF standards track and defined in a number of documents, most importantly RFCs. S/MIME was originally developed by RSA Data Security Inc. The original specification used the recently developed IETF MIME specification with the de facto industry standard PKCS #7 secure message format.
S/MIME provides the following cryptographic security services for electronic messaging applications: authentication, message integrity and non-repudiation of origin (using digital signatures) and privacy and data security (using encryption). S/MIME specifies the application/pkcs7-mime (smime-type "enveloped-data") type for data enveloping (encrypting): the whole (prepared) MIME entity to be enveloped is encrypted and packed into an object which subsequently is inserted into an application/pkcs7-mime MIME entity.
S/MIME functionality is built into the vast majority of modern e-mail software and interoperates between them.
#PGP
Pretty Good Privacy (PGP) is a computer program that provides cryptographic privacy and authentication. PGP is often used for signing, encrypting and decrypting e-mails to increase the security of e-mail communications. It was originally created by Philip Zimmermann in 1991.
PGP and other similar products follow the OpenPGP standard (RFC 4880) for encrypting and decrypting data.
PGP encryption uses a serial combination of hashing, data compression, symmetric-key cryptography, and, finally, public-key cryptography; each step uses one of several supported algorithms. Each public key is bound to a user name and/or an e-mail address. The first version of this system was generally known as a web of trust to contrast with the X.509 system which uses a hierarchical approach based on certificate authority and which was added to PGP implementations later. Current versions of PGP encryption include both options through an automated key management server.
-Compatibility-
As PGP evolves, PGP systems that support newer features and algorithms are able to create encrypted messages that older PGP systems cannot decrypt, even with a valid private key. Thus, it is essential that partners in PGP communication understand each other's PGP capabilities or at least agree on PGP settings.
-Digital signatures-
PGP supports message authentication and integrity checking. The latter is used to detect whether a message has been altered since it was completed (the message integrity property), and the former to determine whether it was actually sent by the person/entity claimed to be the sender (a digital signature). In PGP, these are used by default in conjunction with encryption, but can be applied to plaintext as well. The sender uses PGP to create a digital signature for the message with either the RSA or DSA signature algorithms. To do so, PGP computes a hash (also called a message digest) from the plaintext, and then creates the digital signature from that hash using the sender's private keys.
Security in Web
#SSL
What is SSL?
SSL is the ubiquitous security protocol used in almost 100% of secure Internet transactions. Essentially,SSL transforms a typical reliable transport protocol (such as TCP) into a secure communications channel suitable for conducting sensitive transactions.i The SSL protocol defines the methods by which a secure communications channel can be established—it does not indicate which cryptographic algorithms need to be used. SSL supports many different algorithms, and serves as a framework whereby cryptography can be used in a convenient and distributed manner.
Any application that needs to transmit data over an unsecured network such
as the Internet or a company intranet is a potential candidate for SSL. SSL provides security, and moreimportantly, peace of mind. When using SSL, you can be fairly sure that your data are safe from eavesdroppers and tampering.
SSL is relatively new to the embedded world because it has been too complex for traditional embeddedsystems microprocessors to handle. However, starting with Rev. A of the Rabbit 3000 microprocessor, hardware assistance has been added to speed up some of the more complex SSL cryptography operations, making SSL a viable solution in a market where standard (usually complex) security protocols have not traditionally been supported. The applications for embedded applications are as numerous as those for the PC world.
#SSH
Secure Shell or SSH is a network protocol that allows data to be exchanged using a secure channel between two networked devices.[1] Used primarily on Linux and Unix based systems to access shell accounts, SSH was designed as a replacement for Telnet and other insecure remote shells, which send information, notably passwords, in plaintext, leaving them open for interception.[2] The encryption used by SSH provides confidentiality and integrity of data over an insecure network, such as the Internet.
SSH uses public-key cryptography to authenticate the remote computer and allow the remote computer to authenticate the user, if necessary.
SSH is typically used to log into a remote machine and execute commands, but it also supports tunneling, forwarding TCP ports and X11 connections; it can transfer files using the associated SFTP or SCP protocols.SSH uses the client-server model.
The standard TCP port 22 has been assigned for contacting SSH servers.
An SSH client program is typically used for establishing connections to an SSH daemon accepting remote connections. Both are commonly present on most modern operating systems, including Mac OS X, Linux, FreeBSD, Solaris and OpenVMS. Proprietary, freeware and open source versions of various levels of complexity and completeness exist.
#HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is a combination of the Hypertext Transfer Protocol with the SSL/TLS protocol to provide encryption and secure identification of the server. HTTPS connections are often used for payment transactions on the World Wide Web and for sensitive transactions in corporate information systems. HTTPS should not be confused with Secure HTTP (S-HTTP) specified in RFC 2660
#SFTP
SFTP, or secure FTP, is a program that uses SSH to transfer files. Unlike standard FTP, it encrypts both commands and data, preventing passwords and sensitive information from being transmitted in the clear over the network. It is functionally similar to FTP, but because it uses a different protocol, you can't use a standard FTP client to talk to an SFTP server,can connect to an FTP server with a client that supports only SFTP.
Posted by SeCuRiTy LiFe.. at 6:09 PM 0 comments
LEC 5:: Security in network
Definition
+A computing network is a computing environment with more than one independent processors
+May be multiple users per system
+Distance between computing systems is not considered (a communications media problem)
+Size of computing systems is not relevant
What is a Network can Provide?
~ Logical interface function
~ Sending messages
~ Receiving messages
~ Executing program
~ Obtaining status information
~ Obtaining status information on other network users and their status
Type of Network
One way to categorize the different types of computer network designs is by their scope or scale. For historical reasons, the networking industry refers to nearly every type of design as some kind of area network. Common examples of area network types are:
* LAN - Local Area Network
* WLAN - Wireless Local Area Network
* WAN - Wide Area Network
* MAN - Metropolitan Area Network
* SAN - Storage Area Network, System Area Network, Server Area Network, or sometimes Small Area Network
Who Couse Security Problem
Ò
Ò~Hacker
Ò~Spy
Ò~Student
Ò~Businessman
Ò~Ex-employee
Ò~Stockbroker
Ò~Terrorist
Network Security Control
Ò~Encryption
Ò~Strong Authentication
Ò~IPSec,VPN,SSH
Ò~Kerberos
Ò~Firewall
Ò~Intrusion Detection System (IDS)
Ò~Intrusion Prevention System (IPS)
Ò~Honeypot
Encryption
Encryption is the conversion of data into a form, called a ciphertext, that cannot be easily understood by unauthorized people. Decryption is the process of converting encrypted data back into its original form, so it can be understood.
Encryption is the most effective way to achieve data security . To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. Unencrypted data is called plain text; encrypt data is referred to as cipher text
Hacking And Preventation
Ò~motivated by thrill of access and status
É @hacking community a strong meritocracy
É @status is determined by level of competence
Ò~benign intruders might be tolerable
É @do consume resources and may slow performance
É @can’t know in advance whether benign or malign
Ò~IDS / IPS / VPNs can help counter
Ò~awareness led to establishment of CERTs
É @collect / disseminate vulnerability info / responses
Covering Track
Ò~Every activity is logged
~Syslog, accesslog, eventlog,
Intrusion Detection Systems
• classify intrusion detection systems (IDSs)
as:
• Host-based IDS: monitor single host activity
• Network-based IDS: monitor network traffic
• logical components:
• sensors - collect data
• analyzers - determine if intrusion has occurred
• user interface - manage / direct / view IDS
IDS Principles
• assume intruder behavior differs from
legitimate users
• expect overlap as shown
• observe deviations
from past history
• problems of:
• false positives
• false negatives
• must compromise
Honeyports
In computer terminology, a honeypot is a trap set to detect, deflect, or in some manner counteract attempts at unauthorized use of information systems. Generally it consists of a computer, data, or a network site that appears to be part of a network, but is actually isolated, (un)protected, and monitored, and which seems to contain information or a resource of value to attackers.
A honeypot is valuable as a surveillance and early-warning tool. While it is often a computer, a honeypot can take other forms, such as files or data records, or even unused IP address space. A honeypot that masquerades as an open proxy to monitor and record those using the system is a sugarcane. Honeypots should have no production value, and hence should not see any legitimate traffic or activity. Whatever they capture can then be surmised as malicious or unauthorized. One practical implication of this is honeypots that thwart spam by masquerading as the type of systems abused by spammers.
Honeypots can be classified based on their deployment and based on their level of involvement. Based on the deployment, honeypots may be classified as
1. Production Honeypots
2. Research Honeypots
Posted by SeCuRiTy LiFe.. at 5:49 PM 0 comments
Sunday, October 4, 2009
LEC 4:: AUTHENTICATION & ACCES CONTROL
Authentication
*Password
*Biometric
Access control
*Matrix
*List
*Unix access control
-Verification of identity of someone who generated some data
-Relates to identity verification
-classifications of identity verification:
+by something known e.g. password
+by something possessed e.g. smart card, passport
+by physical characteristics (biometrics) e.g. finger prints, palm prints, retina, voice
+by a result of involuntary action : signature
Password
Protection of passwords
Don’t keep your password to anybody
Don’t write or login your password at everywhere
Etc.
Choosing a good password
Criteria:
-Hard to guess and easy to remember
Characteristics of a good password
-Not shorter than six characters
-Not patterns from the keyboard
Etc.
Calculations on password
*Password population, N =rs
*Probability of guessing a password = 1/N
*Probability of success, P=nt/N
Techniques for guessing passwords
*Try default passwords.8
*Try all short words, 1 to 3 characters long.
*Try all the words in an electronic dictionary(60,000).
*Collect information about the user’s hobbies, family names, birthday, etc.
*Try user’s phone number, social security number, street address, etc.
*Try all license plate numbers
*Use a Trojan horse
*Tap the line between a remote user and the host system.
What is Biometric?
*The term is derived from the Greek words bio (= life) and metric (= to measure)
*Biometrics is the measurement and statistical analysis of biological data
*In IT, biometrics refers to technologies for measuring and analysing human body characteristics for authentication purposes
*Definition by Biometrics Consortium – automatically recognising a person using distinguishing traits
Verification vs Identification
*Verification (one-to-one comparison) –confirms a claimed identity
-Claim identity using name, user id, …
*Identification (one-to-many comparison) – establishes the identity of a subject from a set of enrolled persons
-Employee of a company?
-Member of a club?
-Criminal in forensics database?
Static vs. dynamic biometric methods
*Static (also called physiological) biometric methods – authentication based on a feature that is always present
*Dynamic (also called behavioural) biometric methods – authentication based on a certain behaviour pattern
Classification of biometric methods
Static
Fingerprint recognition
Retinal scan
Iris scan
Hand geometry
Dynamic
Signature recognition
Speaker recognition
Keystroke dynamics
Biometric system model
Posted by SeCuRiTy LiFe.. at 8:09 AM 0 comments
Wednesday, August 12, 2009
Lec 3 :: Modern Cryptography
21 SYABAAN 1430
12 OGOS 2009( WEDNESDAY )
Today i learn about:-
* modern cryptography algorithm
* Block & Stream
* DES
* AES
* MAC
* Digital Signature
>> DES
* Provides a high level of security
* The security depends on keys, not the secrecy of the algorithm
* The security is capable of being evaluated
* The algorithm is completely specified and easy to understand
* It is efficient to use and adaptable
* Must be available to all users
* Must be exportable
Posted by SeCuRiTy LiFe.. at 7:05 AM 0 comments
Monday, August 3, 2009
LAB 2::The Goals of Information Technology Security
The goals of Information Technology Security.
In general the term “Security” is use to describe the quality
or state of being secure that is to be free from danger or to be
protected from those who would do harm, intentionally or otherwise.
In Information Security it is refer to the protection of information and
the systems and hardware that use, store, and transmit that
information.
Information security involves the security in an organization
regarding the application security, policies involves and Information
Technology infrastructure to create a secure and protected
computing environment for an organization. The goals of an
Information security are confidentiality, integrity and availability. In
contemporary computer network environments, another goal to be
achieved is to provide legitimate use of resources which ensuring
that resources are from the original source.
On this lab, we do a lab 2 on my own lactop.
TASK 1- Using NTFS to Secure Local Resources.
1. Open your winserv03 virtual machine
2. Log on to the Windows 2003 server as Administrator.
3. Click [Start].
4. Click [Run].
5. Type cmd to invoke the command line. (The FAT partition in
this lab will be designated as drive letter D.)
6. At the command line type chkntfs d: to verify that the drive
is not using NTFS. You will see the m7. To convert a FAT disk to NTFS you need to type at the
command line convert d: /fs:ntfs
7. If the drive has a volume label, enter it when prompted.
Windows will then convert the drive to NTFS. Note: If you
convert the system partition you will have to reboot for the
conversion to take place.
8. At the command line type chkntfs d: to verify that the drive
is now NTFS.essage, “D: is not
9. Close all Windows and log off.
TASK 2::Data Confidentiality.
Once a secure file system is installed, you can begin to think about
data confidentiality. Data confidentiality refers to making sure that
only those intended to have access to certain data actually have
that access. With the FAT file system, this is not possible at the
local level, but with NTFS you can lock down both folders and files
locally. NTFS can be used to protect data from intruders who may
have physical access to the computer containing the data. In this
lab, you will create a folder and files, assign NTFS permissions,
then verify whether or not the data is confidential.
Creating user account
1. Two user-level accounts: User1 and User2
a. To create user account go to [Start] |
[Administrative Tools] | [Computer Management].
b. Choose [Local User and Groups] and double click
on the [user] folder.
c. To create new user right click on the pane and from
the pop-up menu choose [New User] and fill up the
necessary information such as username and
password (use easy to remember password e.g.
abc123)
Posted by SeCuRiTy LiFe.. at 9:58 PM 0 comments
Lec 2- Autentication and Basic Cryptography
Definition of Authentication
Authentication is any process by which a system verifies the identity of a User who wishes to access it. Since Access Control is normally based on the identity of the User who requests access to a resource, Authentication is essential to effective Security.
Authentication may be implemented using Credentials, each of which is composed of a User ID and Password. Alternately, Authentication may be implemented with Smart Cards, an Authentication Server or even a Public Key Infrastructure.
Definition of Password
A secret series of characters that enables a user to access a file, computer, or program. On multi-user systems, each user must enter his or her password before the computer will respond to commands. The password helps ensure that unauthorized users do not access the computer. In addition, data files and programs may require a password.
Ideally, the password should be something that nobody could guess. In practice, most people choose a password that is easy to remember, such as their name or their initials. This is one reason it is relatively easy to break into most computer systems.
A Password is a secret word or code, which a user must supply during a Login to demonstrate that he is, in fact, the person he claims to be. It is one-half of a typical set of Credentials used in Authentication. The other half is the User ID.
To choose a good password.
A good password is one that's hard to guess, yet easy to remember. So here are the top 10 ways to choose a password, in roughly increasing difficulty. If you don't use any of the first 5, you're well on your way. The stats are very rough estimates (for comparison purposes, an 8-character password is used for most calculations):
1. Default (same as none):
o Many programs and services assign a default password . Change this to a new password immediately.
o examples: password, superuser
2. 10 Common passwords:
o god, love, lust, money, private, qwerty, secret, sex, snoopy, & (surprise!) password
3. Personal info:
o your name, initials, location (zip code), birthday, pets, license plate
family/friend's names (including maiden), locations, birthdays, pets
word/number combinations of any of the above
o Ego-related; examples: guru, master, wizard
o Favorite: Music (group names, albums), Fiction/Nonfiction/Comic books/characters, Movie/TV/Cartoon characters & titles
o Dumb Hollywood movie-people think all passwords are of this variety
4. Categories:
o Double-words; examples: kittykitty, johnjohn
o Funny/nonsense/jargon words; examples: wassup, bzzzzz, foobar
o Insults; examples: biteme, eatdirt
o Keyboard sequences; examples: asdfg, qweasd, poiqwe
o Obscene words; examples: (use your imagination)
o Passwords based on host name (for people with lots of passwords)
for example, if the system is named 'cat' an obvious password is catpass
o Reversals; examples: terces, wordpass, nhojnhoj
5. Dictionary & Foreign Language words:
o If you can find your word here, it's not a very good password.
o Common Passwords - Various Languages
Dan Klein - Browsable and categorized lists of English words
DEC Collection - compressed lists of common English words
o stats: There's 200,000+ words in the English language (most people use around 10,000-40,000). As a guesstimate, there's some 32,000 8-letter words/phrases.
For some word lists, see The Electronic Alveary
6. Mixed-Case Dictionary Words (alternating UPPER-lower case letters)
o examples: paSSworD, PLaceBO
o stats: If a word has 2 letters, there's 4 (22) ways to capitalize it (at, At, aT, AT). If a word has 8 letters, there's 256 ways. Similar combinations (2letters) apply to each word in the dictionary. Guesstimate: There's around 32,000 8-letter words, which gives 8 million (32,000 x 256) mixed-case 8-letter passwords
7. Mixed-case Word with Number(s)
o examples: 9fiNgeRS, loVELy68
o stats: Tacking on a number from 0-9 before or after a word gives 20 more variations to the password. Using 00-99 before or after the word, gives 200 variations. Guesstimate: there's some 19,000 6-letter words, and 243 million variations (19,000 x 64 x 200) of 6-letter-word 2-number passwords.
8. Mixed-case Word(s)/Letter(s)
o Combining words and/or extra letters
o examples: GUessTHis, BiKeFisH
o stats: We're talking pretty big numbers here. Around 53 trillion (528) 8-letter mixed-case passwords (i.e. aaaaaaaa, aaaaaaaA, aaaaaaAa, ..., ZZZZZZZZ)
9. Mixed-case Words/Numbers/Letters
o examples: No50WaY2, puT863MoX
o variant: Hacker/IRC/License-plate jargon
examples: H4x0rD00dZ, UR2good4Me, FXR1stR8
o stats: OK, my mind's swimming, there's somewhere around 218 trillion (628) 8-letter/number passwords
o It takes an average of 5 seconds to crack this kind of password on a Windows machine; considerably longer on BSD or Linux.
10. Random characters
o examples: qs3UIs82, k38#0J$dA
o note: some programs and services only allow letters and numbers, some include dashes ('-'); the best allow any character
o stats: Assuming 94 'type-able' characters, there's 6 gazillion (948 = 6.1 quadrillion [US]) different 8-character passwords. There's not as many 7-character passwords, but there's some 9-character ones still available, if you hurry.
In general:
• No password is uncrackable.
o The best you can do is make it difficult and non-trivial to determine your password.
o What's the worst password? The one you've forgotten.
• Whatever method you choose, it's a good idea to change your password often.
o The more important the password, the more often it should be changed.
o Why? If someone is attempting a brute-force attack on your password, the hope is that you're changing it to something they've already tried and found to be wrong.
• The longer the password, the harder it is to 'guess.'
o note: many systems limit passwords to 8 characters.
• Some clever people are foregoing brute-force hacks (e.g. dictionary attacks), in favor of 'social engineering' to obtain passwords.
o If somebody calls or emails, requesting your password, it's a dumb idea to give it to them.
o Of course nobody would sticky-note a password to their monitor, or under a keyboard.
Do:
• Change your password every three to six months. Changing once every term should be considered an absolute minimum frequency.
• Use both upper and lower case letters.
• Use numbers and special symbols (!@#$) with letters.
• Create simple mnemonics (memory aids) or compounds that are easily remembered, yet hard to decipher:
o ``3laR2s2uaPA$$WDS!'' for ``Three-letter acronyms are too short to use as passwords!''
o ``IwadaSn,atCwt2bmP,btc't.'' for ``It was a dark and stormy night, and the crackers were trying to break my password, but they couldn't.''
o ``HmPwaCciaCccP?'' for ``How many passwords would a cracker crack if a cracker could crack passwords?''
• Use two or more words together (Yet_Another_Example).
• Use misspelled words (WhutdooUmeenIkan'tSpel?).
• Use a minimum of eight characters. You may use up to 255 characters on Athena, and generally the longer the password, the more secure it is.
Never!
Finally, NEVER write your password down anywhere, nor share your password with anyone, including your best friend, your academic advisor, or an on-line consultant!
Bad Passwords
A password is bad when it is:
• Easy for humans or computers to guess.
• Hard for you to remember.
Good Passwords
A password is good when it is:
• Hard for humans or computers to guess.
• Easy for you to remember.
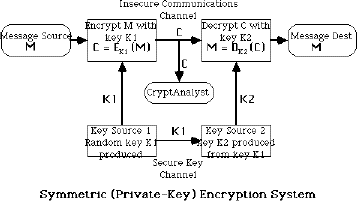
What is cryptograpy?
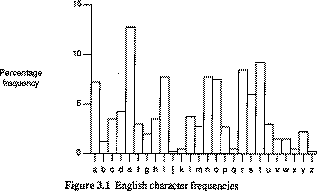
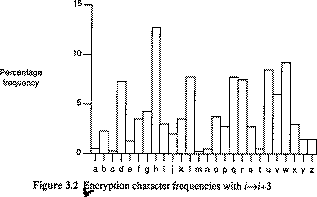
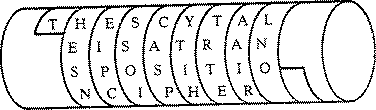
Everyone has secrets; some have more than others. When it becomes necessary to transmit those secrets from one point to another, it's important to protect the information while it's in transit. Cryptography presents various methods for taking legible, readable data, and transforming it into unreadable data for the purpose of secure transmission, and then using a key to transform it back into readable data when it reaches its destination.
Predating computers by thousands of years, cryptography has its roots in basic transposition ciphers, which assigns each letter of the alphabet a particular value. A simple example is to assign each letter a progressively higher number, where A=1, B=2, and so forth. Using this formula for example, the word "wiseGEEK", once encrypted, would read "23 9 19 5 7 5 5 11". During World War Two, machines were invented that made the ciphers more complicated and difficult to break, and today, computers have made cryptography even stronger still.
The Secure Sockets Layer (SSL) is a common encryption protocol used in e-commerce. When you make a purchase over the Internet, this is the technology the merchant uses to make sure you can safely transmit your credit card information. Using this protocol, your computer and the online merchant's computer agree to create a type of private "tunnel" through the public Internet. This process is called the "handshake." When you see a URL in your Web browser that starts with "https" instead of "http", it is a secure connection that is using SSL.
Some methods of cryptography used a "secret key" to allow the recipient to decrypt the message. The most common secret key cryptosystem is the Data Encryption Standard (DES), or the more secure Triple-DES which encrypts the data three times.
More common are systems that use a public key cryptography system, such as the Diffie-Hellman key agreement protocol. This system uses two keys that work together; a public one, which anyone can access, and a private one, which is kept secret by the party receiving the data. When you want to send a secure message to someone, you encrypt that message using the recipient's public key. But once encrypted, the recipient must use his or her private key to decrypt it.
The goal of cryptography extends beyond merely making data unreadable, it also extends into user authentication, that is, providing the recipient with assurance that the encrypted message originated from a trusted source. Hash functions are sometimes used in conjunction with private key or public key cryptography. This is a type of one-way encryption, which applies an algorithm to a message, such that the message itself cannot be recovered. Unlike key-based cryptography, the goal of the hash function is not to encrypt data for later decryption, but to create a sort of digital fingerprint of a message. The value derived from applying the hash function can be re-calculated at the receiving end, to ensure that the message has not been tampered with during transit. Then, key-based cryptography is applied to decipher the message.
The study of cryptography is advancing steadily, and scientists are rapidly creating mechanisms that are more difficult to break. The most secure type of cryptography yet may be quantum cryptography, a method that has not yet been perfected, which instead of using a key, relies on the basic laws of physics, and the movement and orientation of photons to establish a connection that is absolutely secure and unbreakable.
Encryption - Basic Concepts
1 Introduction
There are many different methods of encryption available ranging from the extremely trivial ROT-13 (which believe it or not was originally developed by Julias Caesar, albeit in a slightly different form that could have been called ROT-3), through medium strength techniques such as DES, and finally onto highly secure algorithms such as Blowfish.
The principle behind any encryption technique remains the same, i.e. to rearrange data held within a file to ensure the data is not easily readable by others.
The unencrypted file is often referred to as Plaintext, and the encrypted file as Ciphertext.
The process in principle is straightforward. In it's simplest form, an algorithm to encrypt needs two basic components :-
The data itself
An encryption/decryption key
The key can be thought of as a password consisting of hundreds, or even thousands of bits to ensure it is difficult to break the encrypted file.
Obviously it would not be easy to remember say a 2048 bit key every time you want to encrypt or decrypt a file. Various techniques are used within encryption routines to generate large keys that are held in encrypted form and are decrypted by entering a shorter password, which is a lot easier to remember.
2 A Simple Example
As a simple example of a weak encryption method, consider a file that consists of a single line of text :-
Hello
This would actually be stored on your hard disk as the following series of bytes :-
48 65 6C 6C 6F
Suppose we decide to encrypt this file using the key (or password) :-
Where
This would actually be stored on your hard disk as the following series of bytes :-
57 68 65 72 65
We could encrypt our file by applying an XOR (exclusive or) function to it. This looks at individual bits within each byte and compares the data bits with the key bits. If both the data and key individual bits are he same, then the output of the XOR function is a zero and vice versa. The following truth table illustrates the XOR function :-
Input A Input B Output X
0 0 0
0 1 1
1 0 1
1 1 0
If we use the XOR function on our file containing the text "Hello" using the key "Where" we end up with the following set of numbers :-
1F 0D 09 1E 0A
Obviously, anyone reading that file would not be able to decipher the word "Hello" without having access to our key. We can decrypt the file by applying the XOR function to the encrypted file using the same key we used to encrypt it.
The same technique can be used to encrypt a file of any size by applying the key to successive chunks of data.
Although this method of encryption would protect your file from the eyes of most people, if you were targetted by experts, and you had plenty of encrypted files for them to go to work on, your files wouldn't remain safe for long.
There are many methods an experienced cryptologist can use to break encryption techniques. This is not an area I will discuss on this site as it would more than double the contents. If you are interested in such methods, a search on the web will find plenty of sites to read. Take a look at the Links section as a starting point for your research.
3 Public and Private Keys
Many encryption algorithms use a single (private) key for both encryption and decryption. This is fine for encrypting data on your own hard drive as you will be the only person who will require access to the key. However, there may be times where you want to send an encrypted file to someone else, or that person might want to send you an encrypted file.
Obviously you would need to release your key to that person to enable them to decrypt your file. However, this would also mean that if you have used the same key to encrypt other information on your own computer, then that information is no longer safe. If your key fell into the hands of the authorites and they raided your house, they would be able to read all of your encrypted data.
More importantly, if your methods of communication are being monitored by the authorities, they could quite easily intercept both the key and encrypted file you might send to another person.
The problem of key distribution was solved in the 1970's by the development of cryptographic algorithms that use two keys. One of the keys is used for encryption, and is called the public key. It is safe to release this key to anyone as it can't be used to decrypt a file. The second key is your private key and is used to decrypt files.
Your private key should never be divulged to anyone !
Say for example that you want to send encrypted messages via email to a friend. Obviously your friend will also want to be able to send encrypted messages back to you. So how does this work ?
You release your public key to your friend and vice versa. It does not matter if the keys are intercepted by the authorities as they can only be used to encrypt data. Once you have exchanged public keys, you can send encrypted data (using your friends public key for encryption) knowing that if it is intercepted by the authorities, they will not be able to decrypt the data without your friends private key, which of course (s)he never divulges to anyone. Similarly, your friend can encrypt a message using your public key for encryption, which means that it can only be decrypted by you with your private key.
4 Key Size
So what key size should you use ?
This is a frequently asked question that is not adequately covered by most articles on encryption.
Choosing a suitable key size is vital to ensure your data remains safe from the experienced cryptologer who might be hired to crack your data.
Assuming you have taken the time to pick a strong encryption algorithm that allows you to choose key sizes, and you want to protect very sensitive data for many years, I would advise the following :-
Encryption Type Minimum Key Length in Bits
Public Key 8192
Private Key 4096
That might seem a little over the top if you have read other articles on encryption key size. However, who knows what is round the corner in terms of increases in networked computing power and new techniques to break encryption !
RSA is a strong encryption algorithm that can be used for public and private key cryptography. 512 bit keys have already been broken and 1024 bit keys are expected to be compromised within the next year.
Be warned that usually the bigger the better when it comes to key size, however, that is not always true. For example, the Triple-DES encryption method only uses 56 bit keys and has not yet been broken. The 56 bit key is a bit of a misnomer here as Triple-DES encrypts three times in a variety of ways.
I'll be talking about key sizes in more detail in the Algorithms section.
5 Digital Signatures
In the public key scenario, there is a major weakness in that you have made your public key available to anyone who can intercept it. So when you get an encrypted message from your friend, how do you know it actually originated from him/her ?
Maybe it is an attempt by the authorities to get you to reply back and incriminate yourself...after all, your public key can be used by anyone !
This is where the concept of the Digital Signature comes in.
There are various methods used to add a Signature to a message you encrypt, using your own private key to do this which ensures that your friend can be certain the message originated from you (as only you have access to your private key). The algorithms used for adding such a signature also ensure that when your friend decrypts your message, he is certain that the data has not been tampered with in any way after you have sent it.
However, let me make one important point clear.
If you do send a digitally signed message, make sure you know exactly who you are sending it to. Under UK law, such messages can be used as evidence and are considered proof that you actually were the sender. If you admit to doing something illegal in such a message, you might find yourself in very deep waters !
If you are in any doubt as to who you are sending a message to, and it contains incriminating evidence, it might be better to send it from an email account which you have previously setup (and only ever access) via a Phreaked connection.
See the Phreaking section for further details on this.
6 Other Issues
There are many other concepts involved in cryptography, e.g. Digital Certificates to name one phrase you might have come across before.
However, these are all outside the scope of this article, which after all has been written with the intention of showing you how to hide encrypted data on your own hard drive.
The Links section has many references to sites that discuss cryptography in depth.
In the UK, there are moves afoot to make it law that a person has to provide his password to the authorities on request, ie Key Escrow. This is causing a lot of controversy and the government appear to be chopping and changing their ideas on what they want to do with this.
What many people don't realise is that the police in effect already have this power under the Police and Criminal Evidence Act 1984 (PACE). The Police can sieze computer equipment if they get a search warrant from the Courts. Section 20 of PACE states that powers of seizure conferred on a constable who has entered premises under statutory authority shall be construed as a power to require any information contained in a computer and accessible from the premises to be produced in a form in which it can be taken away and in which it is visible and legible.
Posted by SeCuRiTy LiFe.. at 12:59 AM 0 comments
Lab 1-Introduction to Virtualization & VMware
During this lab session we learn about virtualization & vmware. What is vmware? Virtual machine software from VMware, that allows multiple copies of the same operating system or several different operating systems to run in the same x86-based machine. For years, VMware has been the leader in virtualization software.
By the end of this section of the practical, we should be able
to:
• Understand What is Virtualization
• Install VMware Workstation
• Understand the VMware Workstation Configuration
• Creating disk image on VMware Workstation
• Installing Windows Server 2003 on disk image
VMware Workstation installation
This is simple step by step on how to install VMware Workstation:
1.Download VMware Workstation from http://www.vmware.com/download/ws/. Then, double click the VMware launcher to start the installation wizards.
2. Click NEXT and choose Typical setup type
3. Choose the location for VMware Workstation installation. Then, click NEXT
4. Configure the shortcuts for the VMware Workstation and click NEXT
5. Click INSTALL. This will take several minutes to finish
6. Enter the serial number for the VMware Workstation.
7. Click FINISH and restart the computer.
Posted by SeCuRiTy LiFe.. at 12:52 AM 0 comments
Monday, July 20, 2009
Chapter 1: INTRODUCTION TO INFORMATION SECURITY
Information to security involves the security in organization regarding the application security, policies involves and IT infrastructure to create a secure and protected computing environment for an organization. Security service is use to describe technology based security functions provided in system and products. Traditionally, information security has been considered to have three fundamental objectives.
1. Confidentiality of information
2. Intergrity of data
3. Availability of information
SECURITY POLICY
A security policies is a set of rules to apply to all security relevant activities in a security domain. A security domain is typically the set of processing and communications resources belonging to one organization or in other words is the scope of a single security policies.
THREATS & SAFEGUARDS
Threats – a person, thing, event or idea which poses some danger to an asset in terms of that asset’s from threats.
Attack – an actual realization of threats
Safeguards- physical control, mechanism, policies and and procuders that protect assets from threats.
Vulnerabilities- weakness in safeguard or the absence of safeguards
Risk-a measure of the cost of a realized vulnerability that incorporates the probability of a successful attack.
Categories of threats
• Deliberate threats. E.g. hacker penetration
• Accidental. E .g message sent in error to the wrong address.
METHODS OF DEFENSE
1. Prevent it: by blocking the attack or closing the vulnerability
2. Deter it: by making the attack harder but not impossible
3. Deflect it: by making another target more attractive
4. Detect it: either as it happens or sometime after the fact
5. Recover : from its effects
CONTROL
Control are used to preserving confidentiality, integrity and availability.
Control can be:
Encryption coding to transform data to be unintelligible to the outside observer.
Software controls: development control, operating system controls and internal program control.
Hardware control: to lock limiting access to theft protection
Policies : legal and ethical controls.
Physical control: easiest, effective and least expensive way.
SECURITY SERVICES
Authentication service: provide assurance of the identity of some entity.
Access control service: protects against unauthorized use or manipulation of resources
Data confidentiality services: protect against information being disclosed or revealed to unauthorized entities.
Data integrity services: protect against data being changed, deleted or substituted without authorization
Non-repudiation: protect against one party to a communication exchange later falsely denying that the exchange occurred.
SECURITY MECHANISM
Security mechanisms exist to provide and support security services. There are two classes:
Specific security mechanism-used to provide specific security services.
Pervasive security mechanism-not specific to particular services.
Specific security mechanism
i. Encipherment
ii. Digital signature
iii. Access control mechanism
iv. Data intergrity mechanism
v. Authentication exchanges
vi. Traffic padding
vii. Routing control
viii. Notarization
Pervasive security mechanism
i. Trusted functionality
ii. Security label
iii. Event detection
iv. Security audit trail
v. Security recovery
Posted by SeCuRiTy LiFe.. at 7:40 PM 0 comments
Sunday, July 19, 2009
SeCuRiTy LiFe
Salam...
Blog nie aku buat khas untuk memenuhi kehendak lecturer aku..EN ZAKI MASUD BAGI subject NETWORK SECURITY.
Posted by SeCuRiTy LiFe.. at 11:05 PM 0 comments






 .
. e and
e and  share no divisors other than
share no divisors other than  .
.  , where lcm is the
, where lcm is the  and
and  ,
, .
.

 .
. ,
, .
.



 e.g., by computing the
e.g., by computing the  :
: 


 .
. Because of this multiplicative property a
Because of this multiplicative property a  and so the effect of
and so the effect of 
 ie mapping is
ie mapping is