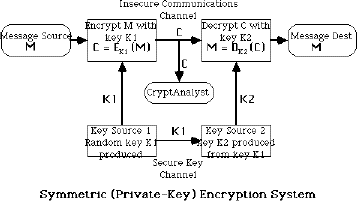
The goals of Information Technology Security.
In general the term “Security” is use to describe the quality
or state of being secure that is to be free from danger or to be
protected from those who would do harm, intentionally or otherwise.
In Information Security it is refer to the protection of information and
the systems and hardware that use, store, and transmit that
information.
Information security involves the security in an organization
regarding the application security, policies involves and Information
Technology infrastructure to create a secure and protected
computing environment for an organization. The goals of an
Information security are confidentiality, integrity and availability. In
contemporary computer network environments, another goal to be
achieved is to provide legitimate use of resources which ensuring
that resources are from the original source.
On this lab, we do a lab 2 on my own lactop.
TASK 1- Using NTFS to Secure Local Resources.
1. Open your winserv03 virtual machine
2. Log on to the Windows 2003 server as Administrator.
3. Click [Start].
4. Click [Run].
5. Type cmd to invoke the command line. (The FAT partition in
this lab will be designated as drive letter D.)
6. At the command line type chkntfs d: to verify that the drive
is not using NTFS. You will see the m7. To convert a FAT disk to NTFS you need to type at the
command line convert d: /fs:ntfs
7. If the drive has a volume label, enter it when prompted.
Windows will then convert the drive to NTFS. Note: If you
convert the system partition you will have to reboot for the
conversion to take place.
8. At the command line type chkntfs d: to verify that the drive
is now NTFS.essage, “D: is not
9. Close all Windows and log off.
TASK 2::Data Confidentiality.
Once a secure file system is installed, you can begin to think about
data confidentiality. Data confidentiality refers to making sure that
only those intended to have access to certain data actually have
that access. With the FAT file system, this is not possible at the
local level, but with NTFS you can lock down both folders and files
locally. NTFS can be used to protect data from intruders who may
have physical access to the computer containing the data. In this
lab, you will create a folder and files, assign NTFS permissions,
then verify whether or not the data is confidential.
Creating user account
1. Two user-level accounts: User1 and User2
a. To create user account go to [Start] |
[Administrative Tools] | [Computer Management].
b. Choose [Local User and Groups] and double click
on the [user] folder.
c. To create new user right click on the pane and from
the pop-up menu choose [New User] and fill up the
necessary information such as username and
password (use easy to remember password e.g.
abc123)
Monday, August 3, 2009
LAB 2::The Goals of Information Technology Security
Posted by SeCuRiTy LiFe.. at 9:58 PM
Subscribe to:
Post Comments (Atom)





 .
. e and
e and  share no divisors other than
share no divisors other than  .
.  , where lcm is the
, where lcm is the  and
and  ,
, .
.

 .
. ,
, .
.



 e.g., by computing the
e.g., by computing the  :
: 


 .
. Because of this multiplicative property a
Because of this multiplicative property a  and so the effect of
and so the effect of 
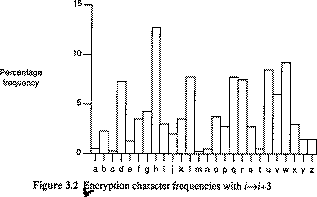
 ie mapping is
ie mapping is 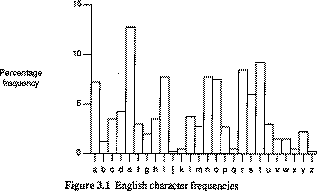


0 comments:
Post a Comment