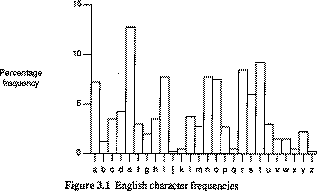
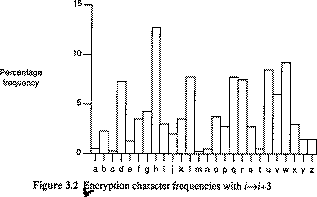
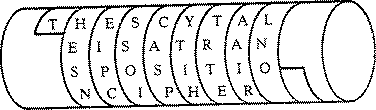
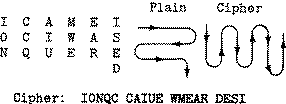Information to security involves the security in organization regarding the application security, policies involves and IT infrastructure to create a secure and protected computing environment for an organization. Security service is use to describe technology based security functions provided in system and products. Traditionally, information security has been considered to have three fundamental objectives.
1. Confidentiality of information
2. Intergrity of data
3. Availability of information
SECURITY POLICY
A security policies is a set of rules to apply to all security relevant activities in a security domain. A security domain is typically the set of processing and communications resources belonging to one organization or in other words is the scope of a single security policies.
THREATS & SAFEGUARDS
Threats – a person, thing, event or idea which poses some danger to an asset in terms of that asset’s from threats.
Attack – an actual realization of threats
Safeguards- physical control, mechanism, policies and and procuders that protect assets from threats.
Vulnerabilities- weakness in safeguard or the absence of safeguards
Risk-a measure of the cost of a realized vulnerability that incorporates the probability of a successful attack.
Categories of threats
• Deliberate threats. E.g. hacker penetration
• Accidental. E .g message sent in error to the wrong address.
METHODS OF DEFENSE
1. Prevent it: by blocking the attack or closing the vulnerability
2. Deter it: by making the attack harder but not impossible
3. Deflect it: by making another target more attractive
4. Detect it: either as it happens or sometime after the fact
5. Recover : from its effects
CONTROL
Control are used to preserving confidentiality, integrity and availability.
Control can be:
Encryption coding to transform data to be unintelligible to the outside observer.
Software controls: development control, operating system controls and internal program control.
Hardware control: to lock limiting access to theft protection
Policies : legal and ethical controls.
Physical control: easiest, effective and least expensive way.
SECURITY SERVICES
Authentication service: provide assurance of the identity of some entity.
Access control service: protects against unauthorized use or manipulation of resources
Data confidentiality services: protect against information being disclosed or revealed to unauthorized entities.
Data integrity services: protect against data being changed, deleted or substituted without authorization
Non-repudiation: protect against one party to a communication exchange later falsely denying that the exchange occurred.
SECURITY MECHANISM
Security mechanisms exist to provide and support security services. There are two classes:
Specific security mechanism-used to provide specific security services.
Pervasive security mechanism-not specific to particular services.
Specific security mechanism
i. Encipherment
ii. Digital signature
iii. Access control mechanism
iv. Data intergrity mechanism
v. Authentication exchanges
vi. Traffic padding
vii. Routing control
viii. Notarization
Pervasive security mechanism
i. Trusted functionality
ii. Security label
iii. Event detection
iv. Security audit trail
v. Security recovery
Monday, July 20, 2009
Chapter 1: INTRODUCTION TO INFORMATION SECURITY
Posted by SeCuRiTy LiFe.. at 7:40 PM 0 comments
Sunday, July 19, 2009
SeCuRiTy LiFe
Salam...
Blog nie aku buat khas untuk memenuhi kehendak lecturer aku..EN ZAKI MASUD BAGI subject NETWORK SECURITY.
Posted by SeCuRiTy LiFe.. at 11:05 PM 0 comments
Subscribe to:
Posts (Atom)





 .
. e and
e and  share no divisors other than
share no divisors other than  .
.  , where lcm is the
, where lcm is the  and
and  ,
, .
.

 .
. ,
, .
.



 e.g., by computing the
e.g., by computing the  :
: 


 .
. Because of this multiplicative property a
Because of this multiplicative property a  and so the effect of
and so the effect of 
 ie mapping is
ie mapping is