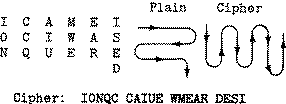21 SYABAAN 1430
12 OGOS 2009( WEDNESDAY )
Today i learn about:-
* modern cryptography algorithm
* Block & Stream
* DES
* AES
* MAC
* Digital Signature
>> DES
* Provides a high level of security
* The security depends on keys, not the secrecy of the algorithm
* The security is capable of being evaluated
* The algorithm is completely specified and easy to understand
* It is efficient to use and adaptable
* Must be available to all users
* Must be exportable
Wednesday, August 12, 2009
Lec 3 :: Modern Cryptography
Posted by SeCuRiTy LiFe.. at 7:05 AM 0 comments
Monday, August 3, 2009
LAB 2::The Goals of Information Technology Security
The goals of Information Technology Security.
In general the term “Security” is use to describe the quality
or state of being secure that is to be free from danger or to be
protected from those who would do harm, intentionally or otherwise.
In Information Security it is refer to the protection of information and
the systems and hardware that use, store, and transmit that
information.
Information security involves the security in an organization
regarding the application security, policies involves and Information
Technology infrastructure to create a secure and protected
computing environment for an organization. The goals of an
Information security are confidentiality, integrity and availability. In
contemporary computer network environments, another goal to be
achieved is to provide legitimate use of resources which ensuring
that resources are from the original source.
On this lab, we do a lab 2 on my own lactop.
TASK 1- Using NTFS to Secure Local Resources.
1. Open your winserv03 virtual machine
2. Log on to the Windows 2003 server as Administrator.
3. Click [Start].
4. Click [Run].
5. Type cmd to invoke the command line. (The FAT partition in
this lab will be designated as drive letter D.)
6. At the command line type chkntfs d: to verify that the drive
is not using NTFS. You will see the m7. To convert a FAT disk to NTFS you need to type at the
command line convert d: /fs:ntfs
7. If the drive has a volume label, enter it when prompted.
Windows will then convert the drive to NTFS. Note: If you
convert the system partition you will have to reboot for the
conversion to take place.
8. At the command line type chkntfs d: to verify that the drive
is now NTFS.essage, “D: is not
9. Close all Windows and log off.
TASK 2::Data Confidentiality.
Once a secure file system is installed, you can begin to think about
data confidentiality. Data confidentiality refers to making sure that
only those intended to have access to certain data actually have
that access. With the FAT file system, this is not possible at the
local level, but with NTFS you can lock down both folders and files
locally. NTFS can be used to protect data from intruders who may
have physical access to the computer containing the data. In this
lab, you will create a folder and files, assign NTFS permissions,
then verify whether or not the data is confidential.
Creating user account
1. Two user-level accounts: User1 and User2
a. To create user account go to [Start] |
[Administrative Tools] | [Computer Management].
b. Choose [Local User and Groups] and double click
on the [user] folder.
c. To create new user right click on the pane and from
the pop-up menu choose [New User] and fill up the
necessary information such as username and
password (use easy to remember password e.g.
abc123)
Posted by SeCuRiTy LiFe.. at 9:58 PM 0 comments
Lec 2- Autentication and Basic Cryptography
Definition of Authentication
Authentication is any process by which a system verifies the identity of a User who wishes to access it. Since Access Control is normally based on the identity of the User who requests access to a resource, Authentication is essential to effective Security.
Authentication may be implemented using Credentials, each of which is composed of a User ID and Password. Alternately, Authentication may be implemented with Smart Cards, an Authentication Server or even a Public Key Infrastructure.
Definition of Password
A secret series of characters that enables a user to access a file, computer, or program. On multi-user systems, each user must enter his or her password before the computer will respond to commands. The password helps ensure that unauthorized users do not access the computer. In addition, data files and programs may require a password.
Ideally, the password should be something that nobody could guess. In practice, most people choose a password that is easy to remember, such as their name or their initials. This is one reason it is relatively easy to break into most computer systems.
A Password is a secret word or code, which a user must supply during a Login to demonstrate that he is, in fact, the person he claims to be. It is one-half of a typical set of Credentials used in Authentication. The other half is the User ID.
To choose a good password.
A good password is one that's hard to guess, yet easy to remember. So here are the top 10 ways to choose a password, in roughly increasing difficulty. If you don't use any of the first 5, you're well on your way. The stats are very rough estimates (for comparison purposes, an 8-character password is used for most calculations):
1. Default (same as none):
o Many programs and services assign a default password . Change this to a new password immediately.
o examples: password, superuser
2. 10 Common passwords:
o god, love, lust, money, private, qwerty, secret, sex, snoopy, & (surprise!) password
3. Personal info:
o your name, initials, location (zip code), birthday, pets, license plate
family/friend's names (including maiden), locations, birthdays, pets
word/number combinations of any of the above
o Ego-related; examples: guru, master, wizard
o Favorite: Music (group names, albums), Fiction/Nonfiction/Comic books/characters, Movie/TV/Cartoon characters & titles
o Dumb Hollywood movie-people think all passwords are of this variety
4. Categories:
o Double-words; examples: kittykitty, johnjohn
o Funny/nonsense/jargon words; examples: wassup, bzzzzz, foobar
o Insults; examples: biteme, eatdirt
o Keyboard sequences; examples: asdfg, qweasd, poiqwe
o Obscene words; examples: (use your imagination)
o Passwords based on host name (for people with lots of passwords)
for example, if the system is named 'cat' an obvious password is catpass
o Reversals; examples: terces, wordpass, nhojnhoj
5. Dictionary & Foreign Language words:
o If you can find your word here, it's not a very good password.
o Common Passwords - Various Languages
Dan Klein - Browsable and categorized lists of English words
DEC Collection - compressed lists of common English words
o stats: There's 200,000+ words in the English language (most people use around 10,000-40,000). As a guesstimate, there's some 32,000 8-letter words/phrases.
For some word lists, see The Electronic Alveary
6. Mixed-Case Dictionary Words (alternating UPPER-lower case letters)
o examples: paSSworD, PLaceBO
o stats: If a word has 2 letters, there's 4 (22) ways to capitalize it (at, At, aT, AT). If a word has 8 letters, there's 256 ways. Similar combinations (2letters) apply to each word in the dictionary. Guesstimate: There's around 32,000 8-letter words, which gives 8 million (32,000 x 256) mixed-case 8-letter passwords
7. Mixed-case Word with Number(s)
o examples: 9fiNgeRS, loVELy68
o stats: Tacking on a number from 0-9 before or after a word gives 20 more variations to the password. Using 00-99 before or after the word, gives 200 variations. Guesstimate: there's some 19,000 6-letter words, and 243 million variations (19,000 x 64 x 200) of 6-letter-word 2-number passwords.
8. Mixed-case Word(s)/Letter(s)
o Combining words and/or extra letters
o examples: GUessTHis, BiKeFisH
o stats: We're talking pretty big numbers here. Around 53 trillion (528) 8-letter mixed-case passwords (i.e. aaaaaaaa, aaaaaaaA, aaaaaaAa, ..., ZZZZZZZZ)
9. Mixed-case Words/Numbers/Letters
o examples: No50WaY2, puT863MoX
o variant: Hacker/IRC/License-plate jargon
examples: H4x0rD00dZ, UR2good4Me, FXR1stR8
o stats: OK, my mind's swimming, there's somewhere around 218 trillion (628) 8-letter/number passwords
o It takes an average of 5 seconds to crack this kind of password on a Windows machine; considerably longer on BSD or Linux.
10. Random characters
o examples: qs3UIs82, k38#0J$dA
o note: some programs and services only allow letters and numbers, some include dashes ('-'); the best allow any character
o stats: Assuming 94 'type-able' characters, there's 6 gazillion (948 = 6.1 quadrillion [US]) different 8-character passwords. There's not as many 7-character passwords, but there's some 9-character ones still available, if you hurry.
In general:
• No password is uncrackable.
o The best you can do is make it difficult and non-trivial to determine your password.
o What's the worst password? The one you've forgotten.
• Whatever method you choose, it's a good idea to change your password often.
o The more important the password, the more often it should be changed.
o Why? If someone is attempting a brute-force attack on your password, the hope is that you're changing it to something they've already tried and found to be wrong.
• The longer the password, the harder it is to 'guess.'
o note: many systems limit passwords to 8 characters.
• Some clever people are foregoing brute-force hacks (e.g. dictionary attacks), in favor of 'social engineering' to obtain passwords.
o If somebody calls or emails, requesting your password, it's a dumb idea to give it to them.
o Of course nobody would sticky-note a password to their monitor, or under a keyboard.
Do:
• Change your password every three to six months. Changing once every term should be considered an absolute minimum frequency.
• Use both upper and lower case letters.
• Use numbers and special symbols (!@#$) with letters.
• Create simple mnemonics (memory aids) or compounds that are easily remembered, yet hard to decipher:
o ``3laR2s2uaPA$$WDS!'' for ``Three-letter acronyms are too short to use as passwords!''
o ``IwadaSn,atCwt2bmP,btc't.'' for ``It was a dark and stormy night, and the crackers were trying to break my password, but they couldn't.''
o ``HmPwaCciaCccP?'' for ``How many passwords would a cracker crack if a cracker could crack passwords?''
• Use two or more words together (Yet_Another_Example).
• Use misspelled words (WhutdooUmeenIkan'tSpel?).
• Use a minimum of eight characters. You may use up to 255 characters on Athena, and generally the longer the password, the more secure it is.
Never!
Finally, NEVER write your password down anywhere, nor share your password with anyone, including your best friend, your academic advisor, or an on-line consultant!
Bad Passwords
A password is bad when it is:
• Easy for humans or computers to guess.
• Hard for you to remember.
Good Passwords
A password is good when it is:
• Hard for humans or computers to guess.
• Easy for you to remember.
What is cryptograpy?
Everyone has secrets; some have more than others. When it becomes necessary to transmit those secrets from one point to another, it's important to protect the information while it's in transit. Cryptography presents various methods for taking legible, readable data, and transforming it into unreadable data for the purpose of secure transmission, and then using a key to transform it back into readable data when it reaches its destination.
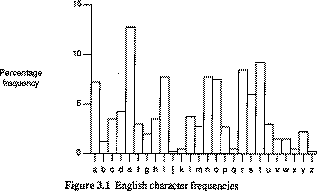
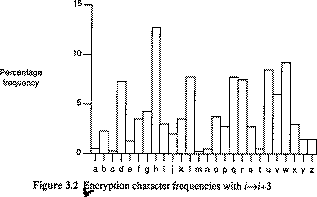
Predating computers by thousands of years, cryptography has its roots in basic transposition ciphers, which assigns each letter of the alphabet a particular value. A simple example is to assign each letter a progressively higher number, where A=1, B=2, and so forth. Using this formula for example, the word "wiseGEEK", once encrypted, would read "23 9 19 5 7 5 5 11". During World War Two, machines were invented that made the ciphers more complicated and difficult to break, and today, computers have made cryptography even stronger still.
The Secure Sockets Layer (SSL) is a common encryption protocol used in e-commerce. When you make a purchase over the Internet, this is the technology the merchant uses to make sure you can safely transmit your credit card information. Using this protocol, your computer and the online merchant's computer agree to create a type of private "tunnel" through the public Internet. This process is called the "handshake." When you see a URL in your Web browser that starts with "https" instead of "http", it is a secure connection that is using SSL.
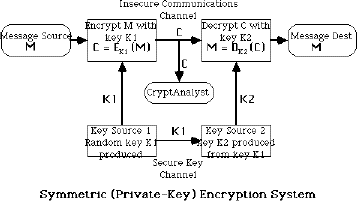
Some methods of cryptography used a "secret key" to allow the recipient to decrypt the message. The most common secret key cryptosystem is the Data Encryption Standard (DES), or the more secure Triple-DES which encrypts the data three times.
More common are systems that use a public key cryptography system, such as the Diffie-Hellman key agreement protocol. This system uses two keys that work together; a public one, which anyone can access, and a private one, which is kept secret by the party receiving the data. When you want to send a secure message to someone, you encrypt that message using the recipient's public key. But once encrypted, the recipient must use his or her private key to decrypt it.
The goal of cryptography extends beyond merely making data unreadable, it also extends into user authentication, that is, providing the recipient with assurance that the encrypted message originated from a trusted source. Hash functions are sometimes used in conjunction with private key or public key cryptography. This is a type of one-way encryption, which applies an algorithm to a message, such that the message itself cannot be recovered. Unlike key-based cryptography, the goal of the hash function is not to encrypt data for later decryption, but to create a sort of digital fingerprint of a message. The value derived from applying the hash function can be re-calculated at the receiving end, to ensure that the message has not been tampered with during transit. Then, key-based cryptography is applied to decipher the message.
The study of cryptography is advancing steadily, and scientists are rapidly creating mechanisms that are more difficult to break. The most secure type of cryptography yet may be quantum cryptography, a method that has not yet been perfected, which instead of using a key, relies on the basic laws of physics, and the movement and orientation of photons to establish a connection that is absolutely secure and unbreakable.
Encryption - Basic Concepts
1 Introduction
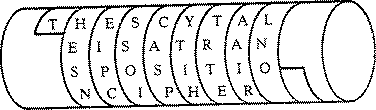
There are many different methods of encryption available ranging from the extremely trivial ROT-13 (which believe it or not was originally developed by Julias Caesar, albeit in a slightly different form that could have been called ROT-3), through medium strength techniques such as DES, and finally onto highly secure algorithms such as Blowfish.
The principle behind any encryption technique remains the same, i.e. to rearrange data held within a file to ensure the data is not easily readable by others.
The unencrypted file is often referred to as Plaintext, and the encrypted file as Ciphertext.
The process in principle is straightforward. In it's simplest form, an algorithm to encrypt needs two basic components :-
The data itself
An encryption/decryption key
The key can be thought of as a password consisting of hundreds, or even thousands of bits to ensure it is difficult to break the encrypted file.
Obviously it would not be easy to remember say a 2048 bit key every time you want to encrypt or decrypt a file. Various techniques are used within encryption routines to generate large keys that are held in encrypted form and are decrypted by entering a shorter password, which is a lot easier to remember.
2 A Simple Example
As a simple example of a weak encryption method, consider a file that consists of a single line of text :-
Hello
This would actually be stored on your hard disk as the following series of bytes :-
48 65 6C 6C 6F
Suppose we decide to encrypt this file using the key (or password) :-
Where
This would actually be stored on your hard disk as the following series of bytes :-
57 68 65 72 65
We could encrypt our file by applying an XOR (exclusive or) function to it. This looks at individual bits within each byte and compares the data bits with the key bits. If both the data and key individual bits are he same, then the output of the XOR function is a zero and vice versa. The following truth table illustrates the XOR function :-
Input A Input B Output X
0 0 0
0 1 1
1 0 1
1 1 0
If we use the XOR function on our file containing the text "Hello" using the key "Where" we end up with the following set of numbers :-
1F 0D 09 1E 0A
Obviously, anyone reading that file would not be able to decipher the word "Hello" without having access to our key. We can decrypt the file by applying the XOR function to the encrypted file using the same key we used to encrypt it.
The same technique can be used to encrypt a file of any size by applying the key to successive chunks of data.
Although this method of encryption would protect your file from the eyes of most people, if you were targetted by experts, and you had plenty of encrypted files for them to go to work on, your files wouldn't remain safe for long.
There are many methods an experienced cryptologist can use to break encryption techniques. This is not an area I will discuss on this site as it would more than double the contents. If you are interested in such methods, a search on the web will find plenty of sites to read. Take a look at the Links section as a starting point for your research.
3 Public and Private Keys
Many encryption algorithms use a single (private) key for both encryption and decryption. This is fine for encrypting data on your own hard drive as you will be the only person who will require access to the key. However, there may be times where you want to send an encrypted file to someone else, or that person might want to send you an encrypted file.
Obviously you would need to release your key to that person to enable them to decrypt your file. However, this would also mean that if you have used the same key to encrypt other information on your own computer, then that information is no longer safe. If your key fell into the hands of the authorites and they raided your house, they would be able to read all of your encrypted data.
More importantly, if your methods of communication are being monitored by the authorities, they could quite easily intercept both the key and encrypted file you might send to another person.
The problem of key distribution was solved in the 1970's by the development of cryptographic algorithms that use two keys. One of the keys is used for encryption, and is called the public key. It is safe to release this key to anyone as it can't be used to decrypt a file. The second key is your private key and is used to decrypt files.
Your private key should never be divulged to anyone !
Say for example that you want to send encrypted messages via email to a friend. Obviously your friend will also want to be able to send encrypted messages back to you. So how does this work ?
You release your public key to your friend and vice versa. It does not matter if the keys are intercepted by the authorities as they can only be used to encrypt data. Once you have exchanged public keys, you can send encrypted data (using your friends public key for encryption) knowing that if it is intercepted by the authorities, they will not be able to decrypt the data without your friends private key, which of course (s)he never divulges to anyone. Similarly, your friend can encrypt a message using your public key for encryption, which means that it can only be decrypted by you with your private key.
4 Key Size
So what key size should you use ?
This is a frequently asked question that is not adequately covered by most articles on encryption.
Choosing a suitable key size is vital to ensure your data remains safe from the experienced cryptologer who might be hired to crack your data.
Assuming you have taken the time to pick a strong encryption algorithm that allows you to choose key sizes, and you want to protect very sensitive data for many years, I would advise the following :-
Encryption Type Minimum Key Length in Bits
Public Key 8192
Private Key 4096
That might seem a little over the top if you have read other articles on encryption key size. However, who knows what is round the corner in terms of increases in networked computing power and new techniques to break encryption !
RSA is a strong encryption algorithm that can be used for public and private key cryptography. 512 bit keys have already been broken and 1024 bit keys are expected to be compromised within the next year.
Be warned that usually the bigger the better when it comes to key size, however, that is not always true. For example, the Triple-DES encryption method only uses 56 bit keys and has not yet been broken. The 56 bit key is a bit of a misnomer here as Triple-DES encrypts three times in a variety of ways.
I'll be talking about key sizes in more detail in the Algorithms section.
5 Digital Signatures
In the public key scenario, there is a major weakness in that you have made your public key available to anyone who can intercept it. So when you get an encrypted message from your friend, how do you know it actually originated from him/her ?
Maybe it is an attempt by the authorities to get you to reply back and incriminate yourself...after all, your public key can be used by anyone !
This is where the concept of the Digital Signature comes in.
There are various methods used to add a Signature to a message you encrypt, using your own private key to do this which ensures that your friend can be certain the message originated from you (as only you have access to your private key). The algorithms used for adding such a signature also ensure that when your friend decrypts your message, he is certain that the data has not been tampered with in any way after you have sent it.
However, let me make one important point clear.
If you do send a digitally signed message, make sure you know exactly who you are sending it to. Under UK law, such messages can be used as evidence and are considered proof that you actually were the sender. If you admit to doing something illegal in such a message, you might find yourself in very deep waters !
If you are in any doubt as to who you are sending a message to, and it contains incriminating evidence, it might be better to send it from an email account which you have previously setup (and only ever access) via a Phreaked connection.
See the Phreaking section for further details on this.
6 Other Issues
There are many other concepts involved in cryptography, e.g. Digital Certificates to name one phrase you might have come across before.
However, these are all outside the scope of this article, which after all has been written with the intention of showing you how to hide encrypted data on your own hard drive.
The Links section has many references to sites that discuss cryptography in depth.
In the UK, there are moves afoot to make it law that a person has to provide his password to the authorities on request, ie Key Escrow. This is causing a lot of controversy and the government appear to be chopping and changing their ideas on what they want to do with this.
What many people don't realise is that the police in effect already have this power under the Police and Criminal Evidence Act 1984 (PACE). The Police can sieze computer equipment if they get a search warrant from the Courts. Section 20 of PACE states that powers of seizure conferred on a constable who has entered premises under statutory authority shall be construed as a power to require any information contained in a computer and accessible from the premises to be produced in a form in which it can be taken away and in which it is visible and legible.
Posted by SeCuRiTy LiFe.. at 12:59 AM 0 comments
Lab 1-Introduction to Virtualization & VMware
During this lab session we learn about virtualization & vmware. What is vmware? Virtual machine software from VMware, that allows multiple copies of the same operating system or several different operating systems to run in the same x86-based machine. For years, VMware has been the leader in virtualization software.
By the end of this section of the practical, we should be able
to:
• Understand What is Virtualization
• Install VMware Workstation
• Understand the VMware Workstation Configuration
• Creating disk image on VMware Workstation
• Installing Windows Server 2003 on disk image
VMware Workstation installation
This is simple step by step on how to install VMware Workstation:
1.Download VMware Workstation from http://www.vmware.com/download/ws/. Then, double click the VMware launcher to start the installation wizards.
2. Click NEXT and choose Typical setup type
3. Choose the location for VMware Workstation installation. Then, click NEXT
4. Configure the shortcuts for the VMware Workstation and click NEXT
5. Click INSTALL. This will take several minutes to finish
6. Enter the serial number for the VMware Workstation.
7. Click FINISH and restart the computer.
Posted by SeCuRiTy LiFe.. at 12:52 AM 0 comments





 .
. e and
e and  share no divisors other than
share no divisors other than  .
.  , where lcm is the
, where lcm is the  and
and  ,
, .
.

 .
. ,
, .
.



 e.g., by computing the
e.g., by computing the  :
: 


 .
. Because of this multiplicative property a
Because of this multiplicative property a  and so the effect of
and so the effect of 
 ie mapping is
ie mapping is