Intruders
Security Intrusion & Detection
Types of IDS
*HIDS
*NIDS
*DIDS
IDS Techniques
SNORT
Honeypots
An Intrusion detection system (IDS) is software and/or hardware designed to detect unwanted attempts at accessing, manipulating, and/or disabling computer systems, mainly through a network, such as the Internet. These attempts may take the form of attacks, as examples, by crackers, malware and/or disgruntled employees. An IDS cannot directly detect attacks within properly encrypted traffic.
An intrusion detection system is used to detect several types of malicious behaviors that can compromise the security and trust of a computer system. This includes network attacks against vulnerable services, data driven attacks on applications, host based attacks such as privilege escalation, unauthorized logins and access to sensitive files, and malware (viruses, trojan horses, and worms).
An IDS can be composed of several components: Sensors which generate security events, a Console to monitor events and alerts and control the sensors, and a central Engine that records events logged by the sensors in a database and uses a system of rules to generate alerts from security events received. There are several ways to categorize an IDS depending on the type and location of the sensors and the methodology used by the engine to generate alerts. In many simple IDS implementations all three components are combined in a single device or appliance.
IDS Terminology
Alert/Alarm- A signal suggesting a system has been or is being attacked [1].
True attack stimulus- An event that triggers an IDS to produce an alarm and react as though a real attack were in progress [1].
False attack stimulus- The event signaling an IDS to produce an alarm when no attack has taken place [1].
False (False Positive)- An alert or alarm that is triggered when no actual attack has taken place [1].
*False negative- A failure of an IDS to detect an actual attack.
*Noise- Data or interference that can trigger a false positive .
*Site policy- Guidelines within an organization that control the rules and configurations of an IDS .
*Site policy awareness- The ability an IDS has to dynamically change its rules and configurations in response to changing environmental activity .
*Confidence value- A value an organization places on an IDS based on past performance and analysis to help determine its ability to effectively identify an attack .
*Alarm filtering- The process of categorizing attack alerts produced from an IDS in
order to distinguish false positives from actual attacks.
Types of Intrusion-Detection systems
There are three main types of systems in which IDS can be used : network, applications and hosts.
In a network-based intrusion-detection system (NIDS), the sensors are located at choke points in network to be monitored, often in the demilitarized zone (DMZ) or at network borders. The sensor captures all network traffic and analyzes the content of individual packets for malicious traffic.
In systems, PIDS and APIDS are used to monitor the transport and protocols for illegal or inappropriate traffic or constructs of a language. For example forged SQL queries attempting to delete database records, virus in emails.
In a host-based system, the sensor usually consists of a software agent, which monitors all activity of the host on which it is installed. For example attempt to modify the master boot record, keylogger, file access.
Hybrids for the two later systems also exist.
Network intrusion detection system (NIDS)
It is an independent platform which identifies intrusions by examining network traffic and monitors multiple hosts. Network Intrusion Detection Systems gain access to network traffic by connecting to a hub, network switch configured for port mirroring, or network tap. An example of a NIDS is Snort.
Protocol-based intrusion detection system (PIDS)
It consists of a system or agent that would typically sit at the front end of a server, monitoring and analyzing the communication protocol between a connected device (a user/PC or system) and the server. For a web server this would typically monitor the HTTPS protocol stream and understand the HTTP protocol relative to the web server/system it is trying to protect. Where HTTPS is in use then this system would need to reside in the "shim", or interface, between where HTTPS is un-encrypted and immediately prior to its entering the Web presentation layer.
Application protocol-based intrusion detection system (APIDS)
It consists of a system or agent that would typically sit within a group of servers, monitoring and analyzing the communication on application specific protocols. For example, in a web server with a database this would monitor the SQL protocol specific to the middleware/business logic as it transacts with the database.
Host-based intrusion detection system (HIDS)
It consists of an agent on a host which identifies intrusions by analyzing system calls, application logs, file-system modifications (binaries, password files, capability/acl databases) and other host activities and state. An example of a HIDS is OSSEC.
Hybrid intrusion detection system
It combines two or more approaches. Host agent data is combined with network information to form a comprehensive view of the network. An example of a Hybrid IDS is Prelude.
Intrusion detection systems can also be system-specific using custom tools and honeypots.
Thursday, October 22, 2009
LEC 9:: Intrusion Detection System
Posted by SeCuRiTy LiFe.. at 6:21 PM
Subscribe to:
Post Comments (Atom)





 .
. e and
e and  share no divisors other than
share no divisors other than  .
.  , where lcm is the
, where lcm is the  and
and  ,
, .
.

 .
. ,
, .
.



 e.g., by computing the
e.g., by computing the  :
: 


 .
. Because of this multiplicative property a
Because of this multiplicative property a  and so the effect of
and so the effect of 
 ie mapping is
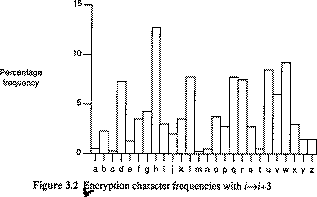
ie mapping is 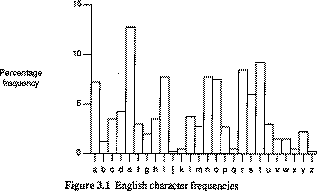


0 comments:
Post a Comment