Definition
+A computing network is a computing environment with more than one independent processors
+May be multiple users per system
+Distance between computing systems is not considered (a communications media problem)
+Size of computing systems is not relevant
What is a Network can Provide?
~ Logical interface function
~ Sending messages
~ Receiving messages
~ Executing program
~ Obtaining status information
~ Obtaining status information on other network users and their status
Type of Network
One way to categorize the different types of computer network designs is by their scope or scale. For historical reasons, the networking industry refers to nearly every type of design as some kind of area network. Common examples of area network types are:
* LAN - Local Area Network
* WLAN - Wireless Local Area Network
* WAN - Wide Area Network
* MAN - Metropolitan Area Network
* SAN - Storage Area Network, System Area Network, Server Area Network, or sometimes Small Area Network
Who Couse Security Problem
Ò
Ò~Hacker
Ò~Spy
Ò~Student
Ò~Businessman
Ò~Ex-employee
Ò~Stockbroker
Ò~Terrorist
Network Security Control
Ò~Encryption
Ò~Strong Authentication
Ò~IPSec,VPN,SSH
Ò~Kerberos
Ò~Firewall
Ò~Intrusion Detection System (IDS)
Ò~Intrusion Prevention System (IPS)
Ò~Honeypot
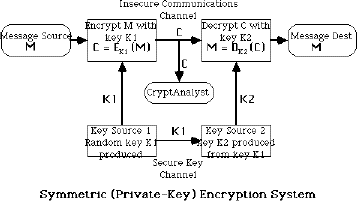
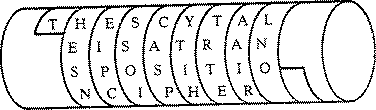
Encryption
Encryption is the conversion of data into a form, called a ciphertext, that cannot be easily understood by unauthorized people. Decryption is the process of converting encrypted data back into its original form, so it can be understood.
Encryption is the most effective way to achieve data security . To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. Unencrypted data is called plain text; encrypt data is referred to as cipher text
Hacking And Preventation
Ò~motivated by thrill of access and status
É @hacking community a strong meritocracy
É @status is determined by level of competence
Ò~benign intruders might be tolerable
É @do consume resources and may slow performance
É @can’t know in advance whether benign or malign
Ò~IDS / IPS / VPNs can help counter
Ò~awareness led to establishment of CERTs
É @collect / disseminate vulnerability info / responses
Covering Track
Ò~Every activity is logged
~Syslog, accesslog, eventlog,
Intrusion Detection Systems
• classify intrusion detection systems (IDSs)
as:
• Host-based IDS: monitor single host activity
• Network-based IDS: monitor network traffic
• logical components:
• sensors - collect data
• analyzers - determine if intrusion has occurred
• user interface - manage / direct / view IDS
IDS Principles
• assume intruder behavior differs from
legitimate users
• expect overlap as shown
• observe deviations
from past history
• problems of:
• false positives
• false negatives
• must compromise
Honeyports
In computer terminology, a honeypot is a trap set to detect, deflect, or in some manner counteract attempts at unauthorized use of information systems. Generally it consists of a computer, data, or a network site that appears to be part of a network, but is actually isolated, (un)protected, and monitored, and which seems to contain information or a resource of value to attackers.
A honeypot is valuable as a surveillance and early-warning tool. While it is often a computer, a honeypot can take other forms, such as files or data records, or even unused IP address space. A honeypot that masquerades as an open proxy to monitor and record those using the system is a sugarcane. Honeypots should have no production value, and hence should not see any legitimate traffic or activity. Whatever they capture can then be surmised as malicious or unauthorized. One practical implication of this is honeypots that thwart spam by masquerading as the type of systems abused by spammers.
Honeypots can be classified based on their deployment and based on their level of involvement. Based on the deployment, honeypots may be classified as
1. Production Honeypots
2. Research Honeypots
Thursday, October 22, 2009
LEC 5:: Security in network
Posted by SeCuRiTy LiFe.. at 5:49 PM
Subscribe to:
Post Comments (Atom)





 .
. e and
e and  share no divisors other than
share no divisors other than  .
.  , where lcm is the
, where lcm is the  and
and  ,
, .
.

 .
. ,
, .
.



 e.g., by computing the
e.g., by computing the  :
: 


 .
. Because of this multiplicative property a
Because of this multiplicative property a  and so the effect of
and so the effect of 
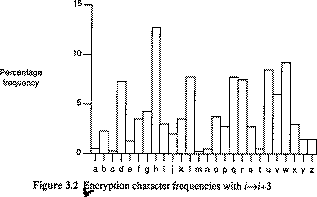
 ie mapping is
ie mapping is 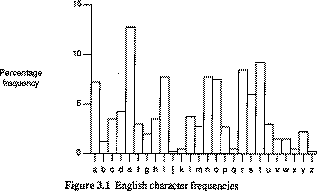

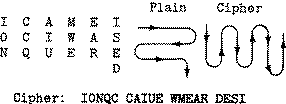

0 comments:
Post a Comment