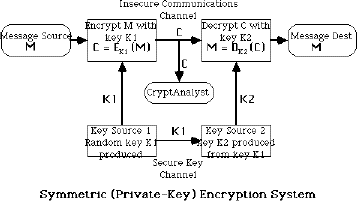
Authentication
*Password
*Biometric
Access control
*Matrix
*List
*Unix access control
-Verification of identity of someone who generated some data
-Relates to identity verification
-classifications of identity verification:
+by something known e.g. password
+by something possessed e.g. smart card, passport
+by physical characteristics (biometrics) e.g. finger prints, palm prints, retina, voice
+by a result of involuntary action : signature
Password
Protection of passwords
Don’t keep your password to anybody
Don’t write or login your password at everywhere
Etc.
Choosing a good password
Criteria:
-Hard to guess and easy to remember
Characteristics of a good password
-Not shorter than six characters
-Not patterns from the keyboard
Etc.
Calculations on password
*Password population, N =rs
*Probability of guessing a password = 1/N
*Probability of success, P=nt/N
Techniques for guessing passwords
*Try default passwords.8
*Try all short words, 1 to 3 characters long.
*Try all the words in an electronic dictionary(60,000).
*Collect information about the user’s hobbies, family names, birthday, etc.
*Try user’s phone number, social security number, street address, etc.
*Try all license plate numbers
*Use a Trojan horse
*Tap the line between a remote user and the host system.
What is Biometric?
*The term is derived from the Greek words bio (= life) and metric (= to measure)
*Biometrics is the measurement and statistical analysis of biological data
*In IT, biometrics refers to technologies for measuring and analysing human body characteristics for authentication purposes
*Definition by Biometrics Consortium – automatically recognising a person using distinguishing traits
Verification vs Identification
*Verification (one-to-one comparison) –confirms a claimed identity
-Claim identity using name, user id, …
*Identification (one-to-many comparison) – establishes the identity of a subject from a set of enrolled persons
-Employee of a company?
-Member of a club?
-Criminal in forensics database?
Static vs. dynamic biometric methods
*Static (also called physiological) biometric methods – authentication based on a feature that is always present
*Dynamic (also called behavioural) biometric methods – authentication based on a certain behaviour pattern
Classification of biometric methods
Static
Fingerprint recognition
Retinal scan
Iris scan
Hand geometry
Dynamic
Signature recognition
Speaker recognition
Keystroke dynamics
Biometric system model
Sunday, October 4, 2009
LEC 4:: AUTHENTICATION & ACCES CONTROL
Posted by SeCuRiTy LiFe.. at 8:09 AM
Subscribe to:
Post Comments (Atom)





 .
. e and
e and  share no divisors other than
share no divisors other than  .
.  , where lcm is the
, where lcm is the  and
and  ,
, .
.

 .
. ,
, .
.



 e.g., by computing the
e.g., by computing the  :
: 


 .
. Because of this multiplicative property a
Because of this multiplicative property a  and so the effect of
and so the effect of 
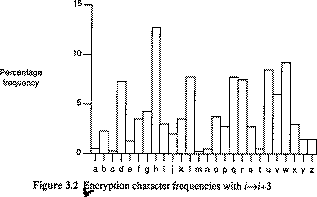
 ie mapping is
ie mapping is 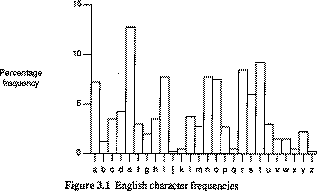


0 comments:
Post a Comment